Many a times when we receive a pcap(especially exploit packs pcaps) for malware analysis purpose we had to do lot of manual work to load it in Fiddler and extract the objects and analyze those. While using windows, i depend on Fiddler for file extraction. I usually import it to fiddler manually and extract the objects. I wanted a command line version of Fiddler import and extract option but unfortunately i couldn’t find those components in the fiddlercore.
After a little bit of digging, i have finally come up with a command line version of this tool that can read the pcap, extract objects and convert the pcap to saz file. I have decided not to release the code because it has lot of code from Fiddler. It’s good if Telerik move the pcap parsing code to FiddlerCore and export the API. So that we all can use it. My blog post is just to show a possibility to do this using FiddlerCore.
I have customized the code to do the following:
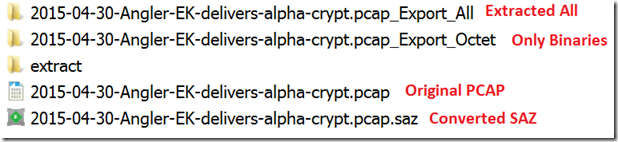
1. pcap2saz
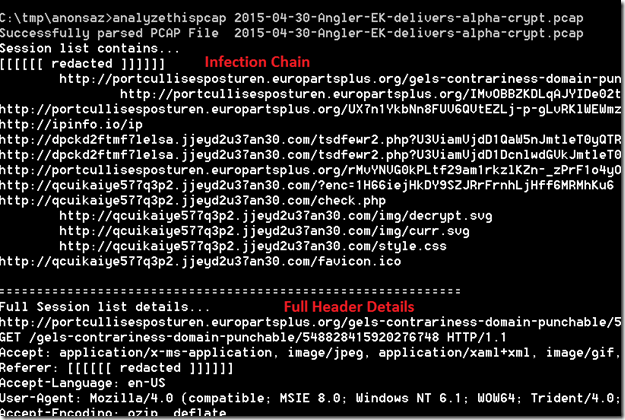
2. Extract the objects (analyzethispcap)
3. Dump the headers
4. Display the infection chain
5. Anonymize SAZ files
Fiddler created SAZ files contains an XML file for each and every
session and that includes source and destination IP’s. Sometimes
we want to share the SAZ files but not these details. Let’s remove it.
Some of the screenshots: