Recently when i got a chance to analyze Neutrino Exploit kit capture, i noticed that Neutrino EK has a detection and check for headless browser and other JS based frameworks. One thing that is interesting about Neutrino EK is all the exploit codes are bundled in a single swf/flash file. Over the network we see only one swf file. Once that swf file is loaded it injects the exploit JS code from swf to browser and executes it. Leaving the EK related details aside, when i saw that headless browser check, i wanted to check whether we can use these headless browser(s)/frameworks for JS code deobfuscation. Looks like EK authors are aware of this kind of techniques and they have added the checks in the exploit code.
Here is the code used in the Neutrino EK:
private function collectBrowserInfo():void{
var _local_2:String = ExternalInterface.call(“function(){return window.navigator.appName;}”);
var _local_10:String = ExternalInterface.call(“function(){return window.navigator.appCodeName;}”);
var _local_5:String = ExternalInterface.call(“function(){return window.navigator.vendor;}”);
var _local_1:Boolean = ExternalInterface.call(“function(){return navigator.cookieEnabled;}”);
var _local_9:Boolean = ExternalInterface.call(“function(){return !!window.callPhantom;}”);
var _local_3:Boolean = ExternalInterface.call(“function(){return !!window.Buffer;}”);
var _local_7:Boolean = ExternalInterface.call(“function(){return !!window.emit;}”);
var _local_8:Boolean = ExternalInterface.call(“function(){return !!window.spawn;}”);
var _local_4:String = ExternalInterface.call(“function(){return navigator.userAgent;}”);
var _local_6:Boolean = ExternalInterface.call(“function(){return /*@cc_on!@*/false || !!document.documentMode;}”);
this.browserInfo = {
“userAgent”:_local_4,
“cntFonts”:Font.enumerateFonts(true).length,
“cpuArchitecture”:Capabilities.cpuArchitecture,
“isDebugger”:Capabilities.isDebugger,
“playerType”:Capabilities.playerType,
“os”:Capabilities.os,
“language”:Capabilities.language,
“flashVer”:Capabilities.version,
“screenColor”:Capabilities.screenColor,
“screenDPI”:Capabilities.screenDPI,
“screenResolutionX”:Capabilities.screenResolutionX,
“screenResolutionY”:Capabilities.screenResolutionY,
“supports32BitProcesses”:Capabilities.supports32BitProcesses,
“supports64BitProcesses”:Capabilities.supports64BitProcesses,
“externalInterface”:ExternalInterface.available,
“isIe”:_local_6,
“cookieEnabled”:_local_1,
“appName”:_local_2,
“appCodeName”:_local_10,
“vendor”:_local_5,
“isPhantom”:_local_9,
“isNodeJs”:_local_3,
“isCouchJs”:_local_7,
“isRhino”:_local_8
};
}
private function checkBrowserInfo():Boolean{
if (true === this.browserInfo.isPhantom)
{
return (false);
};
if (true === this.browserInfo.isNodeJs)
{
return (false);
};
if (true === this.browserInfo.isCouchJs)
{
return (false);
};
if (true === this.browserInfo.isRhino)
{
return (false);
};
if (true === this.browserInfo.isDebugger)
{
return (false);
};
return (true);
}
private function init(e:Event=null):void{
removeEventListener(“addedToStage”, this.init);
this.rtConfigKey = “mrqvlocnq75108”;
this.encryption = new crypt();
if (false === this.checkEnvironment())
{
return;
};
this.collectBrowserInfo();
if (false === this.decodeRtConfig())
{
return;
};
if (false === this.checkBrowserInfo())
{
this.postBotInfo();
return;
};
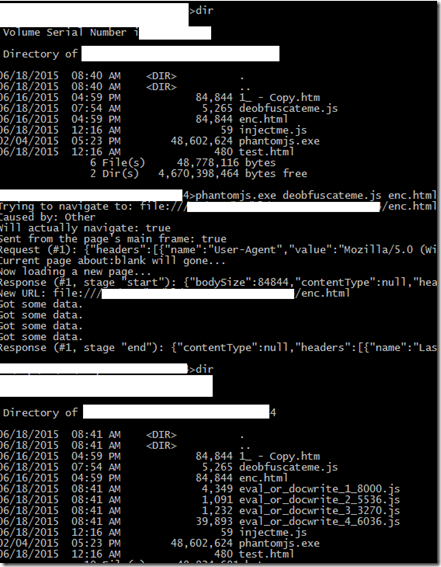
Leaving the EK related information aside, lets see how we can use Phantom JS to deobfuscate the JS code used in the Exploit kits. I used few code from Phantom JS document. Here is the Phantom JS script (It is actually a text file. Download and save the file as .js or .txt)to deobfuscate the code i captured from a exploit delivery capture. Once you executed the script, it will capture the information from window.eval() and document.write(). Here is the screenshot of the execution.
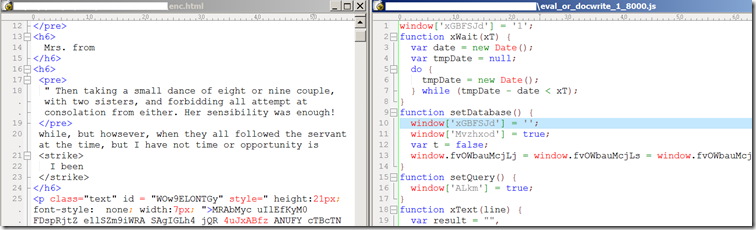
Here is the screenshot of obfuscated and deobfuscated code.
Yes there are many ways to capture the information from these two functions from browser. Using PhantomJS is just another method.


similar post along the same lines,
http://binaryhax0r.blogspot.com/2013/02/phantomjs-against-exploit-kits.html
🙂
Thanks for the link.
Pingback: Deobfuscate Javascript using PhantomJS (Headles...
https://github.com/hidd3ncod3s/PhanthomJS
Pingback: Auto deobfuscate eval packed javascript with node.js – ChiChou's Blog